Agilent's Information Security Approach
Agilent Technologies security program is based on industry standards including ISO 27002 Code of Practice, NIST and the COBIT 5 Framework. Our Policies, Standards and operating procedures provide a comprehensive approach to maintain the confidentiality, integrity, and availability of the data and systems in our environment. Security is a companywide priority and we continuously invest in our People, Processes and Tools to strengthen our security posture to protect both Agilent's and our Customer's data.
To support our companywide approach, we have a dedicated IT Information Security and Risk Management (ISRM) department that is accountable for the following key areas:
Policy, Standards and Operating Procedures |
IT Compliance |
|||
Security Operations |
Risk Management |
|||
Threat and vulnerability management |
Security Awareness |
Our overall security approach focuses on the following five key areas:
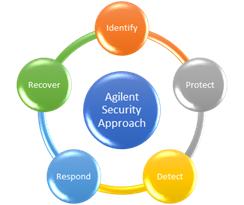
Identify
Identify systems, data, data flows and regulatory requirements and determine appropriate risk management approach
Protect
Implement measures to protect the environment
Detect
Monitor the environment and alert appropriately
Respond
Processes and people in place to address issues and incidents
Recover
Plans and systems to recover from events
Identify
 Understanding our environment, the applicable regulatory requirements, industry and Customer expectations is essential in determining how to appropriately manage the associated risks.
We adopt the following processes and tools to understand Agilent's risk profile and define our on-going security posture and roadmap:
Understanding our environment, the applicable regulatory requirements, industry and Customer expectations is essential in determining how to appropriately manage the associated risks.
We adopt the following processes and tools to understand Agilent's risk profile and define our on-going security posture and roadmap:
Threat Management Process – We monitor for new and changing threats, working with 3rd parties and leveraging threat information published by government agencies.
Customer expectations – Input and requirements from our Customers are fed into our overall security program and where applicable delivered as standard controls and solutions
Risk Assessment Process – All new systems and changes are reviewed to understand and classify the risk of the system. The assessment covers data, privacy, applications, server, network, cloud, logical and physical security.
3rd Party Risk Assessment Process – Agilent assesses 3rd Parties to ensure that they meet our security policies and standards. This is performed using an internal team and 3rd party risk assessment providers.
Asset Register – Agilent maintains a configuration management database which details devices, provides risk ratings, configurations, and classifications.
Regulatory requirements assessment – With a Global presence, workforce and comprehensive product and solution portfolio, Agilent takes an integrated approach to deploy security standards and controls to address those requirements. Today the regulatory requirements include the following:
- SoX
- PCI
- GDPR
- HIPPA
- NIST 800-171
Protect
 Agilent implements measures to provide protection against potential attacks to protect the quality, reliability, and retrievability of our environment and data. These measures can be physical, logical, procedural and/or technical.
Agilent implements measures to provide protection against potential attacks to protect the quality, reliability, and retrievability of our environment and data. These measures can be physical, logical, procedural and/or technical.
Combinations of the following physical, logical, procedural and technical measures are implemented in a layered security approach based on risk.
Environment Controls – The physical security of our facilities, data centers and server rooms is maintained with highly trained security officers and IT professionals.
Network Protection – Firewalls, intrusion detection and prevention, email protection, web content filtering are employed.
Mobile Device Management – Controlling configuration and encryption of all mobile devices that have access to Agilent systems or data.
Encryption – Use of encryption where required, including data at rest and in-transit.
Vulnerability Management – We continuously address identified vulnerabilities in our environment. We use appropriate tools, services and external 3rd parties to complete assessments.
Patch Management – Maintain a process to patch our environment proactively.
Security Awareness Program – Ongoing training programs for our global workforce addressing security, compliance and privacy. These trainings are function and role specific where required and with regular phishing simulations.
Application Security Assessments – Dedicated team to assess developed software prior to deployment into production.
End-point Protection – We deploy the most current anti-virus and advanced malware detection tools. We utilize standard build configurations to ensure that we have appropriate security controls in place.
Identity and Access Management – Robust provisioning and deprovisioning processes, least privilege access, privileged account management, 3rd Party Access controls, multi-factor authentication.
Information Rights Management – Tools are employed to limit access and distribution of data.
High Availability and Back-ups and Disaster Recovery – The Agilent environment is architected to maintain and protect systems and data based on use and data type.
Detect
 The threats that we all face daily keep evolving and that means protection controls on their own are not enough. Detection and alerts on potential risks to the confidentiality, integrity, and availability of the data and systems in our environment is essential.
The threats that we all face daily keep evolving and that means protection controls on their own are not enough. Detection and alerts on potential risks to the confidentiality, integrity, and availability of the data and systems in our environment is essential.
We utilize the following to monitor and detect potential events in our environment:
Security Operations Center (SOC) – Humans monitoring for potential IT security events 24 hours a day, 7 days a week.
IT Operations – 24/7 IT support operations monitoring the health of the environment.
Anti-Virus and Advanced Malware Detection – Network and end-point tools alerting on potential Malware detected in the environment.
Real-Time Network Monitoring – Tools utilizing machine learning to alert on internal network activity.
Event Correlation and anomaly reporting – Big Data solutions correlating operational and security logs to identify and report on anomalies.
Change Management Process – Monitoring changes in the environment to identify potential issues.
Data Base activity monitoring – Monitoring and reporting on database activity.
Threat Monitoring and Hunting – Threat hunting based on industry information and active exploits.
Respond
 Prompt action and response to potential attacks, breaches or disruptions reduces the impact on the confidentiality, integrity, and availability of the environment. Agilent focuses on the people and processes that allow us to respond appropriately.
Prompt action and response to potential attacks, breaches or disruptions reduces the impact on the confidentiality, integrity, and availability of the environment. Agilent focuses on the people and processes that allow us to respond appropriately.
Incident Response Plan – Agilent has a documented security incident response plans that defines roles and responsibilities. This plan includes regular exercises to test against evolving threats and while focusing on continuous improvement.
Incident response team – This dedicated team leads the investigation into security relevant events identified by the SOC, using detection tools or individuals.
IT Incident and Problem management – IT support teams address non-security related incidents and events to ensure a robust environment and maintain availability and integrity of the systems and data.
Reporting Security Issues or concerns
If you are concerned about the security, or have identified an issue, related to Agilent Technologies, our services, products or websites, then please contact our Corporate IT Security Incident Response Team (CITSIRT) – CITSIRT@agilent.com. The team will review your submission and respond to you appropriately.
When contacting the team please provide the following information to aid the investigation.
- Product, service or website Name
- Description of the issue
- Impact of the issue
Recover
 Responding to security events focuses on assessing and addressing the impact of incidents. We also have plans and processes in place to recover the impacted environment to a known, reliable state. Agilent has prioritized recovery processes with supporting tools and teams in place to recover environments following an attack, loss or integrity impact event.
Responding to security events focuses on assessing and addressing the impact of incidents. We also have plans and processes in place to recover the impacted environment to a known, reliable state. Agilent has prioritized recovery processes with supporting tools and teams in place to recover environments following an attack, loss or integrity impact event.
Disaster Recovery Planning – Documented and tested disaster recovery plans based on systems rating.
Communications – Notification process to impacted parties during and after an event
Continuous Improvement – Operational, test and theoretical findings feed into continuous improvement of programs and roadmaps.